H12-723-ENU HCIP-Security-CTSS V3.0 Training Material
H12-723-ENU HCIP-Security-CTSS V3.0 exam is the final exam to achieve your HCIP-Security Certification,the other two exams are H12-721 HCIP-Security-CISN and H12-722 HCIP-Security-CSSN. PassQuestion provides the latest H12-723-ENU HCIP-Security-CTSS V3.0 Training Material to help you pass Huawei H12-723-ENU exam and consolidate your professional knowledge, but also provide you one year free update service.You are guaranteed to pass HCIP-Security-CTSS V3.0 H12-723-ENU exam successfully.

HCIP-Security-CTSS V3.0 H12-723-ENU Exam Overview
If you want to get HCIP-Security Certification, you should learn the knowledge of High reliability of firewalls, advanced VPN applications, network QoS management, application security protection technologies, cloud security technologies, terminal security system deployment, BYOD mobile office systems, wireless network security technologies, etc. Here we will list H12-723-ENU HCIP-Security-CTSS V3.0 exam.
Exam Knowledge Point
HCIP-Security-CTSS V3.0 exam covers the concept of terminal security, Agile Controller Campus system installation planning and deployment, terminal authentication system, WLAN network security technology, terminal security troubleshooting and security system operation and maintenance.
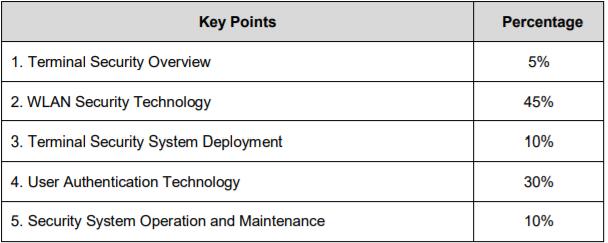
1. Terminal Security Overview
1.1 Necessity of terminal security
1.2 Design Roadmap of the Terminal Security Solution
1.3 Introduction to the Terminal Security System
1.4 Security system maintenance solution
2. WLAN Security Technology
2.1 WLAN Security Threats
2.2 Principles of WIDS/WIPS System
2.3 WLAN User Access Security
2.4 CAWAP Encryption and User Authorization Management
3. Terminal Security System Deployment
3.1 Agile Controller-Campus Installation
3.2 Start the Agile Controller-Campus for the First Time
3.3 High-Reliability Deployment of the Agile Controller-Campus
4. User Authentication Technology
4.1 802.1X Authentication Technology
4.2 MAC Authentication Technology
4.3 SACG Authentication Technology
4.4 Portal Authentication Technology
5. Security System Operation and Maintenance
5.1 User Management Technology
5.2 Agile Network Technology
5.3 eSight Service Management
View Online HCIP-Security-CTSS V3.0 H12-723-ENU Free Questions
1. Which of the following descriptions are correct regarding the strategy of checking account security? (Multiple choices)
A. You can check if there is a weak password.
B. You can check whether the account has joined a specific group.
C. Can't repaired automatically.
D. Can't check whether the password length meets the requirements.
Answer: AB
2. Which of the following are correct for Any Office solution content? (Multiple choices)
A. Provide a unified security portal for enterprise mobility applications on mobile devices.
B. The tunnel is dedicated and viruses can't intrude.
C. Application rapid integration can be extended.
D. Quickly integrate and interface with enterprise application cloud platform.
Answer: ABCD
3. In Layer 2 authentication based on Portal authentication, the client is directly connected to the access device (or only the Layer 2 device exists). The device can learn MAC address of the user and use IP and MAC addresses to identify the user.
A. True
B. False
Answer: A
4. In the terminal host check class policy, you can control the access of the terminal host by checking whether the important subkeys and keys of the registry meet the requirements. Which of the following check results are recorded as violations? (Multiple choices)
A. The registry does not include the "subkeys and key values" enforced by this policy.
B. The registry contains the "subkeys and key values" enforced by this policy.
C. The registry contains "subkeys and key values" prohibited by this policy.
D. The registry does not "subkeys and key values" prohibited by this policy.
Answer: AC
5. In the centralized networking, the database, SM server, SC server and AE server are all installed at the headquarters of the enterprise. This networking mode is applicable to enterprises with a wide geographical distribution of users and a large number of users.
A. True
B. False
Answer: B
6. Visitors can access the network through their registered account. Which of the following is not an account's approval method?
A. Free approval
B. Administrator approval
B. Receptionist Approval
C. Visitor self-approval
Answer: D
- TOP 50 Exam Questions
-
Exam
All copyrights reserved 2025 PassQuestion NETWORK CO.,LIMITED. All Rights Reserved.

