Test Online Free Cisco 350-701 Exam Questions and Answers
The questions for 350-701 were last updated On Mar.07 2024 Get 350-701 Full AccessQuestion No : 1
What are the two most commonly used authentication factors in multifactor authentication? (Choose two)
Answer:
Explanation:
Reference: https://www.cisco.com/c/en/us/products/security/what-is-multi-factor-authentication.html
The two most popular authentication factors are knowledge and inherent (including biometrics like fingerprint, face, and retina scans. Biometrics is used commonly in mobile devices).
Question No : 2
Refer to the exhibit.
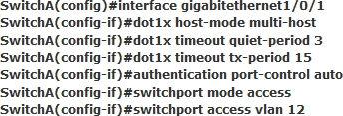
An engineer configured wired 802.1x on the network and is unable to get a laptop to authenticate.
Which port configuration is missing?
Answer:
Question No : 3
Which RADIUS attribute can you use to filter MAB requests in an 802.1 x deployment?
Answer:
Explanation:
Reference: https://www.cisco.com/c/en/us/products/collateral/ios-nx-os-software/identity-based-networkingservices/config_guide_c17-663759.html
Question No : 4
Which flaw does an attacker leverage when exploiting SQL injection vulnerabilities?
Answer:
Explanation:
SQL injection usually occurs when you ask a user for input, like their username/userid, but the user gives(“injects”) you an SQL statement that you will unknowingly run on your database.
For example:
Look at the following example, which creates a SELECT statement by adding a variable (txtUserId) to a selectstring. The variable is fetched from user input (getRequestString):txtUserId = getRequestString(“UserId”);txtSQL = “SELECT * FROM Users WHERE UserId = ” + txtUserId;If user enter something like this: “100 OR 1=1” then the SzQL statement will look like this: SELECT * FROM Users WHERE UserId = 100 OR 1=1;The SQL above is valid and will return ALL rows from the “Users” table, since OR 1=1 is always TRUE. Ahacker might get access to all the user names and passwords in this database.
Question No : 5
Which feature is configured for managed devices in the device platform settings of the Firepower Management Center?
Answer:
Question No : 6
Why would a user choose an on-premises ESA versus the CES solution?
Answer:
Question No : 7
How is ICMP used an exfiltration technique?
Answer:
Question No : 8
Which technology is used to improve web traffic performance by proxy caching?
Answer:
Question No : 9
Which two request of REST API are valid on the Cisco ASA Platform? (Choose two)
Answer:
Explanation:
The ASA REST API gives you programmatic access to managing individual ASAs through a Representational State Transfer (REST) API. The API allows external clients to perform CRUD (Create, Read, Update, Delete) operations on ASA resources; it is based on the HTTPS protocol and REST methodology. All API requests are sent over HTTPS to the ASA, and a response is returned.
Request Structure Available request methods are:
GET C Retrieves data from the specified object.
PUT C Adds the supplied information to the specified object; returns a 404 Resource Not Found error if the object does not exist.
POST C Creates the object with the supplied information.
DELETE C Deletes the specified object
Reference: https://www.cisco.com/c/en/us/td/docs/security/asa/api/qsg-asa-api.html
Question No : 10
What is a characteristic of Firepower NGIPS inline deployment mode?
Answer:
- TOP 50 Exam Questions
-
Exam
All copyrights reserved 2024 PassQuestion NETWORK CO.,LIMITED. All Rights Reserved.

